O2 Script: AntiXSS – Test multiple Encodings
On the topic of AntiXSS here is a script I wrote ages ago called “AntiXSS – Test multiple Encodings.h2” which shows quickly the different behaviours of the different .NET encoding APIs:
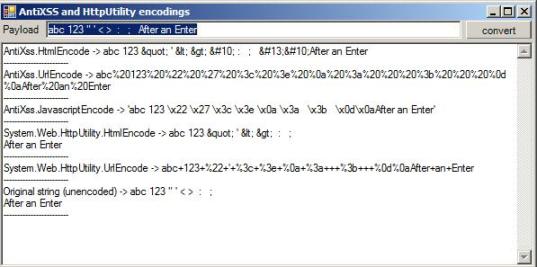
Here is the source of this script:
var topPanel = O2Gui.open<Panel>("AntiXSS and HttpUtility encodings", 600,300);
var result = topPanel.add_TextArea();
Action<string> showEncodings =
(textToEncode)=>{
result.set_Text("");
result.append_Line("AntiXss.HtmlEncode -> {0}".format(AntiXss.HtmlEncode(textToEncode)));
result.append_Line("------------------------");
result.append_Line("AntiXss.UrlEncode -> {0}".format(AntiXss.UrlEncode(textToEncode)));
result.append_Line("------------------------");
result.append_Line("AntiXss.JavascriptEncode -> {0}".format(AntiXss.JavaScriptEncode(textToEncode)));
result.append_Line("------------------------");
result.append_Line("System.Web.HttpUtility.HtmlEncode -> {0}".format(System.Web.HttpUtility.HtmlEncode(textToEncode)));
result.append_Line("------------------------");
result.append_Line("System.Web.HttpUtility.UrlEncode -> {0}".format(System.Web.HttpUtility.UrlEncode(textToEncode)));
result.append_Line("------------------------");
result.append_Line("Original string (unencoded) -> {0}".format(textToEncode));
result.append_Line("------------------------");
};
var testPayload = "abc 123 \" ' < > \n : ; ".line() + "After an Enter";
result.insert_Above<Panel>(20)
.add_LabelAndTextAndButton("Payload", testPayload, "convert", showEncodings);
showEncodings(testPayload);
//return AntiXss.HtmlEncode(payload);
//return "AntiXSSLibrary.dll".assembly().methods();
//using Microsoft.Security.Application
//O2Ref:AntiXSSLibrary.dll
O2 Script with Web Encoder and Decoder (with AntiXss Support)
A couple days ago I needed to do a number of Encodings/Decodings in sequence (Encoded Text -> UrlDecode -> UrlDecode-> HtmlDecode), and since there was no easy way to do that automatically with other tools, I wrote the “Util – Web Encoder (with AntiXss Support).h2” script which looks like this:

Here is the method that runs the transformation (and show what is currently supported)
Func<string,string, string> applyTransformation =
(type, text)=>{
if (type.valid() && text.valid() )
{
switch(type)
{
case "none": break;
case "HtmlDecode": return text.htmlDecode();
case "HtmlEncode": return text.htmlEncode();
case "UrlDecode": return text.urlDecode();
case "UrlEncode": return text.urlEncode();
case "AntiXss.HtmlEncode": return Encoder.HtmlEncode(text);
case "AntiXss.UrlEncode": return Encoder.UrlEncode(text);
case "AntiXss.JavaScriptEncode": return Encoder.JavaScriptEncode(text);
case "AntiXss.CssEncode": return Encoder.CssEncode(text);
case "AntiXss.HtmlAttributeEncode": return Encoder.HtmlAttributeEncode(text);
case "AntiXss.HtmlFormUrlEncode": return Encoder.HtmlFormUrlEncode(text);
case "AntiXss.XmlAttributeEncode": return Encoder.XmlAttributeEncode(text);
case "AntiXss.XmlEncode": return Encoder.XmlEncode(text);
case "AntiXss.VisualBasicScriptEncode": return Encoder.VisualBasicScriptEncode(text);
case "AntiXss.LdapDistinguishedNameEncode": return Encoder.LdapDistinguishedNameEncode(text);
case "AntiXss.LdapFilterEncode": return Encoder.LdapFilterEncode(text);
case "Sanitizer.GetSafeHtml": return Sanitizer.GetSafeHtml(text);
case "Sanitizer.GetSafeHtmlFragment": return Sanitizer.GetSafeHtmlFragment(text);
default:
return text + " not supported: {0}".format(type);
}
}
return text;
};
This uses the latest version of the AntiXSS library, including the new HtmlSanitizationLibrary.dll which has the GetSafeHtml* methods and looks really powerful.
Here is the entire code of this script:
var topPanel = O2Gui.open<Panel>("Util - Web Encoder (with AntiXss Support)",1000,400);
//var topPanel = panel.clear().add_Panel();
var configPanel = topPanel.insert_Above(40,"Config");
var sourceText = topPanel.add_GroupBox("Source Text").add_SourceCodeViewer();
var transformedText = topPanel.insert_Right("Transformed Text").add_SourceCodeViewer();
var transformationsAvailable = new List<string> { "none",
"HtmlDecode", "HtmlEncode","UrlDecode", "UrlEncode",
"AntiXss.HtmlEncode", "AntiXss.UrlEncode", "AntiXss.JavaScriptEncode", "AntiXss.CssEncode",
"AntiXss.HtmlAttributeEncode", "AntiXss.HtmlFormUrlEncode", "AntiXss.XmlAttributeEncode", "AntiXss.XmlEncode",
"AntiXss.VisualBasicScriptEncode","AntiXss.LdapDistinguishedNameEncode", "AntiXss.LdapFilterEncode",
"Sanitizer.GetSafeHtml", "Sanitizer.GetSafeHtmlFragment"};
var transformMode_1 = "";
var transformMode_2 = "";
var transformMode_3 = "";
Func<string,string, string> applyTransformation =
(type, text)=>{
if (type.valid() && text.valid() )
{
switch(type)
{
case "none": break;
case "HtmlDecode": return text.htmlDecode();
case "HtmlEncode": return text.htmlEncode();
case "UrlDecode": return text.urlDecode();
case "UrlEncode": return text.urlEncode();
case "AntiXss.HtmlEncode": return Encoder.HtmlEncode(text);
case "AntiXss.UrlEncode": return Encoder.UrlEncode(text);
case "AntiXss.JavaScriptEncode": return Encoder.JavaScriptEncode(text);
case "AntiXss.CssEncode": return Encoder.CssEncode(text);
case "AntiXss.HtmlAttributeEncode": return Encoder.HtmlAttributeEncode(text);
case "AntiXss.HtmlFormUrlEncode": return Encoder.HtmlFormUrlEncode(text);
case "AntiXss.XmlAttributeEncode": return Encoder.XmlAttributeEncode(text);
case "AntiXss.XmlEncode": return Encoder.XmlEncode(text);
case "AntiXss.VisualBasicScriptEncode": return Encoder.VisualBasicScriptEncode(text);
case "AntiXss.LdapDistinguishedNameEncode": return Encoder.LdapDistinguishedNameEncode(text);
case "AntiXss.LdapFilterEncode": return Encoder.LdapFilterEncode(text);
case "Sanitizer.GetSafeHtml": return Sanitizer.GetSafeHtml(text);
case "Sanitizer.GetSafeHtmlFragment": return Sanitizer.GetSafeHtmlFragment(text);
default:
return text + " not supported: {0}".format(type);
}
}
return text;
};
Action applyTransformations =
()=>{
var originalText = sourceText.get_Text();
var result = applyTransformation(transformMode_1,originalText);
result = applyTransformation(transformMode_2, result);
result = applyTransformation(transformMode_3, result);
transformedText.set_Text(result);
};
sourceText.onTextChange(
(text)=>{
applyTransformations();
});
configPanel.add_Label("Color Code the text as").top(3)
.append_Control<ComboBox>().dropDownList().top(0)
.add_Items(".xml",".html",",cs")
.onSelection((value)=> {
transformedText.editor().setDocumentHighlightingStrategy(value.str());
sourceText.editor().setDocumentHighlightingStrategy(value.str());
})
.selectFirst()
.append_Label("Transform using:").top(3).autoSize()
.append_Control<ComboBox>().dropDownList().top(0).width(170).comboBoxHeight(250)
.add_Items(transformationsAvailable)
.onSelection<string>((value)=> { transformMode_1 = value; applyTransformations(); } )
.selectFirst()
.append_Label("and:").top(3).autoSize()
.append_Control<ComboBox>().dropDownList().top(0).width(170).comboBoxHeight(250)
.add_Items(transformationsAvailable)
.onSelection<string>((value)=> { transformMode_2 = value; applyTransformations(); } )
.append_Label("and:").top(3).autoSize()
.append_Control<ComboBox>().dropDownList().top(0).width(170).comboBoxHeight(250)
.add_Items(transformationsAvailable)
.onSelection<string>((value)=> { transformMode_3 = value; applyTransformations(); } )
;
sourceText.set_Text("this is a <b> test </b>");
return "done";
//using Microsoft.Security.Application
//O2Ref:AntiXSSLibrary.dll
//O2Ref:HtmlSanitizationLibrary.dll

